current location :home>News
Side-channel attacks aim to exfiltrate sensitive information from a chip or a system by measuring the indirect physical parameters (e.g., power consumption, electromagnetic radiation, execution time). In the Internet of Things (IoT) era, counteracting side-channel attacks has become essential for chips that handle sensitive and private information, such as those embedded in mobile phones, smart cards, wearable devices, and many others.
Conventional side-channel attack counteraction techniques require either the circuit redesign to reuse the method or protection embedded into voltage regulators. Such protection techniques suffer from high power overhead. They are fixed (i.e., not upgradable) once manufactured, which limits their usage in energy-autonomous systems of long lifespan and in applications where device replacement is expensive or infeasible.
Assistant Professor Longyang Lin from the School of Microelectronics at the Southern University of Science and Technology (SUSTech), in collaboration with Professor Massimo Alioto’s team at the National University of Singapore (NUS), has recently proposed a novel design-adaptive counteraction approach by exploiting machine learning techniques, enabling both post-silicon upgradability and low power overhead.
Their research work, entitled “Side-Channel Attack Counteraction via Machine Learning-Targeted Power Compensation for Post-Silicon HW Security Patching,” has been presented at the 2022 International Solid-State Circuits Conference (ISSCC), the premier global forum for presenting advances in solid-state circuits and systems-on-a-chip.
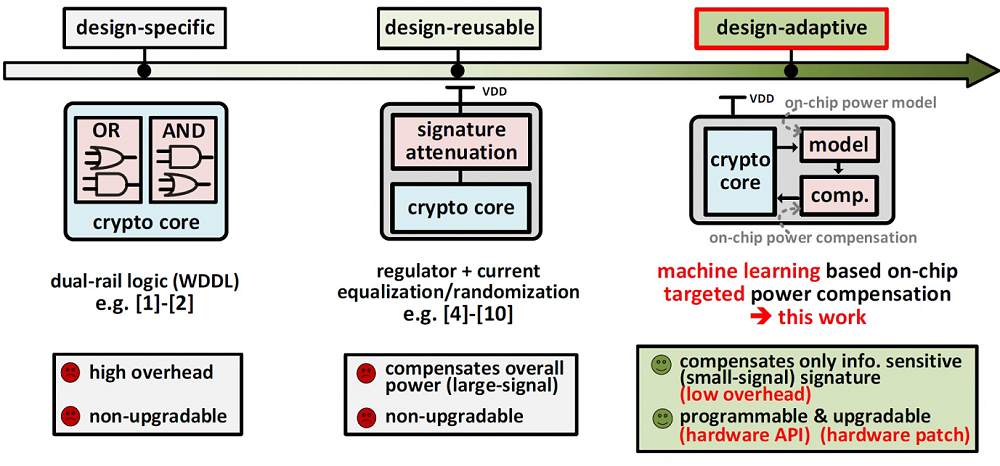
Figure 1. Different categories of side-channel attack counteractions
The proposed design-adaptive counteraction is achieved with low power overhead by introducing a machine-learning-based power estimator with a power compensator targeting only the key-related energy contributions, which also providing post-silicon upgradeability by updating the power model through training. This technique is fully compatible with the conventional standard-cell-based design for easy adoption, system integration, and in-situ protection.
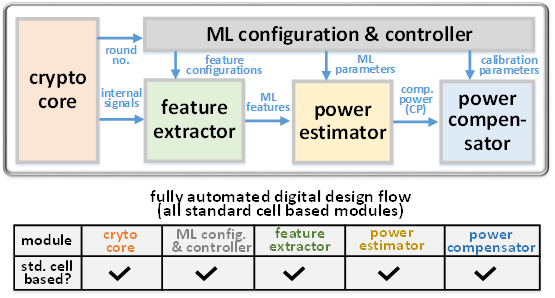
Figure 2. The system architecture of the proposed machine-learning-based protection technique
A 40-nm test chip is designed to demonstrate the proposed machine-learning-based protection technique for different ciphers. Measurement results show that the proposed technique is in line with the best protection methods while incurring only 8.6% power overhead, which is 5.8 times lower than the prior art. In addition, it demonstrates the adaptability across cryptographic implementations and the unique upgradability against new attacks.
Compared with conventional protection techniques, the proposed machine learning-based protection offers a higher degree of flexibility, adaptability to different designs, and upgradability to counteract new attacks, which ultimately maintains high-security standards throughout the device lifespan.